There are many different types of surveillance that exist and if you read on, you will learn about them and the reasons for those specific types. Whether you are a private investigator, someone who wants to be informed, or a concerned citizen, you will have a better grasp of what surveillance entails after reading this article.
Contents
- 1 What is the Definition of Surveillance?
- 2 Overt vs Covert Surveillance
- 3 Overt Surveillance
- 4 Covert Surveillance
- 5 Human Surveillance
- 6 Different types of “Human Surveillance”
- 7 Stationary Surveillance
- 8 Route of Departure Surveillance
- 9 Moving Automobile Surveillance
- 10 Camoflauge Surveillance
- 11 Foot Surveillance
- 12 Boat Surveillance
- 13 Technical Surveillance
- 14 Different Types of Technical Surveillance
- 15 GPS Tracking Devices
- 16 Hidden Camera Devices
- 17 Mechanical Surveillance
- 18 Electronic Surveillance
- 19 Social Media Surveillance
- 20 Postal Service Surveillance
- 21 Internet Surveillance (Corporate Surveillance)
- 22 Aerial Surveillance
- 23 Telephone Surveillance
- 24 Wiretapping
- 25 Stingray Boxes
- 26 Cellular Triangulation
- 27 Cell Phone Tracking
- 28 Historical CSLI (Cell-site location information)
- 29 Real-Time CSLI
- 30 GPS Movement
- 31 Tower Dumps: Reverse Location Search
- 32 Geofence: Reference Location Search
- 33 Biometric Surveillance (or Biometric Security)
- 34 Facial Recognition
- 35 Retina Scanning
- 36 DNA Matching
- 37 Fingerprints
- 38 Satellite Surveillance (photos)
- 39 Military Satellites
- 40 Commercial Satellites
- 41 GPS Satellites
- 42 Scientific Satellites
- 43 Surveillance In the World
What is the Definition of Surveillance?
The definition of surveillance is placing a close watch on something. Another definition is to place close watch over someone or something.
Surveillance can be overt or covert and by a person (Human), technical or electronic.
The word surveillance usually isn’t looked upon in a fond way. As you read on you will see how surveillance can be a positive thing.

Overt vs Covert Surveillance
Surveillance falls into two categories. You have overt surveillance and covert surveillance. Let’s get into the definitions and examples of both types of surveillance.
Overt Surveillance
Overt surveillance is the opposite of covert. Overt surveillance would be having surveillance video cameras outside of your home or business. Overt video cameras are found in stores when you walk in. You might see surveillance cameras in malls or Walmart shopping centers.
Sometimes cameras are there to document activities but also to be a deterrent to crime and illegal activity.
Some people place video cameras in locations in their homes to check on their children when they are not there.
Covert Surveillance
Covert Surveillance Cameras are cameras that are meant to be hidden or discreet. Private investigators use devices like pen cameras or keychain cameras to secure video footage discreetly in public places like stores, restaurants, and parks.
Sometimes hidden cameras are placed in businesses like offices by owners. I have observed this being down to determine if employees were actually working while unsupervised.
Covert surveillance might be conducted in someone’s home. An owner will place hidden cameras in a home to determine if a babysitter is treating their children properly or to see if someone is stealing from their home.

Human Surveillance
Human surveillance involves an individual or individuals physically being present to conduct surveillance efforts. Private investigators commonly conduct surveillance of insurance companies, organizations, businesses, and citizens.
Different types of “Human Surveillance”
Stationary Surveillance
Stationary surveillance generally speaking is a fixed position to view a surveillance location. Preferably these positions are unobstructed but not always. These positions are maintained as long as the integrity of the surveillance is maintained or until the subject of an investigation departs. Mobile Automobile Surveillance is initiated went the subject of an investigation departs a location.
Route of Departure Surveillance
A route of departure surveillance point is a location where an investigator would establish surveillance away from a surveillance point (house, business, etc..) in order to follow the subject after departure.
This type of surveillance position is more passive however can be effective in helping the surveillance investigator go undetected for longer. There are various reasons for taking this position of surveillance.
Moving Automobile Surveillance
When a subject departs a location in a vehicle, on foot or a bike, etc.., an investigator will begin mobile automobile surveillance (investigator will follow the subject in their vehicle).
Camoflauge Surveillance
Camouflage surveillance is simply an investigator conducting surveillance wearing camouflage in an area where the camouflage will blend in. Investigators must make sure not to trespass while conducting surveillance of this nature.
Foot Surveillance
There are situations where investigators need to be on foot to follow individuals in areas where a vehicle is not practical or an option to conduct surveillance. Foot surveillance allows investigators to enter locations with the subject of investigation.
Boat Surveillance
When needed, surveillance can be conducted from a boat as long as surveillance does not invade the privacy of others.

Technical Surveillance
The definition of technical surveillance is the constant or continuous listening of specific individuals with the assistance of covert (technical) technical devices. These different devices can listen to audio, record video, and track items and vehicles (GPS).
Different Types of Technical Surveillance
GPS Tracking Devices
Most people are familiar with the idea of GPS Tracking Devices. Companies and even investigation companies have been know to track the vehicles their employee drive. Companies can track the location of their vehicles and in some cases the speed of travel. Some private investigation companies use these tracking devices on their investigators’ personal vehicles to ensure investigators are where they say they are as some investigators have been known to ghost surveillance assignments (not be on site).
Hidden Camera Devices
There are many devices on the market that can record continuously to a cloud or to memory cards locally on the device.
One recording device that is used by homeowners, and even in offices is a spy camera charger adapter. The device records to a memory card while also allowing the user to view the camera remotely.
A listening device that can be hidden but not remotely accessed is the TileRec audio recorder. If placed in a secure location with a power bank, this device can record audio for up to 145 hours. Some devices can’t charge and work at the same time but the TileRec audio recorder can.
Mechanical Surveillance
Mechanical surveillance relates to surveillance devices that can monitor an area without the monitoring by humans. You may see this in various locations like stores, parking areas, business locations, etc.. This is the overt surveillance that was previously mentioned.
Mechanical surveillance can also be used by private investigators. There are hidden camera devices that use mobile internet cards to provide living view access of remote cameras. These cameras are powered by small motorcycle batteries that can power the hidden camera continuously for 5 to 7 days. The video is recorded to the cloud and is available to view viewed live if needed.
Small cameras can also be used by investigators in a vehicle allowing for unmanned surveillance for several days at a time. The only limitation is the memory card and power source that is used. This camera is the Zetta Z16. If an investigator needs to document a location for extended periods of time to see the coming and going of individuals, this is incredibly ideal. Set up the camera with a power bank power source and document activity without the chance of being detected.
For overt mechanical surveillance cameras for home use, the Ring Camera System has been incredibly reliable for indoor and outdoor surveillance cameras. Ring designed the surveillance system to be monitored from a phone and record when activity is noted. In addition, these cameras can be placed anywhere without a power source as they are recharged with solar panels.
Electronic Surveillance
Electronic surveillance reaches a variety of platforms that you may or may not realize, from Post Office mail tracking to Cell Phone Tracking. Let’s get into the different types of electronic surveillance.
Social Media Surveillance
Private investigators and insurance companies have been known to monitor the social media sites of people and businesses. You may not have realized that the Postal Service was tasked with monitoring Americans’ social media under a program called Internet Covert Operations Program or iCOP.
That type of surveillance has some consequences. Two lawsuits have been filed as a result of some alleged unlawful surveillance including using facial recognition software by Clearview and social media tracking software by Zignal Labs.

Postal Service Surveillance
The Postal Service is known to have partnered with other agencies in the past to open foreign and domestic mail according to a NY Times article written some time ago. Law enforcement agencies need a warrant to open mail.
Another Postal Service surveillance system is place is called Mail Covers or Mail Isolation Control and Tracking Program. This program has Postal Service computers photograph the exterior of every piece of paper mail. At the request of law enforcement, postal workers will record the information on the outside of letters before they are delivered. The Postal Service used to only track mail from people they were concerned about, now they track everyone’s mail according to a quote from Mark Rasch in a New York Times article, founder of the computer crimes unit in the Justice Department.
You may have realized this if you received notifications from the post office. If you do, then you may have received photos of your mail showing you what will be arriving that day.
You can read more about other work the United States Postal Inspection Service here.
Internet Surveillance (Corporate Surveillance)
Internet providers, social media platforms, and search engine giants like Google are tracking all we do on the internet. The pretext for doing this tracking is to better serve the customer (you) with better search results and with better ads..
If you have ever talked about a specific topic with someone and then happened to see an ad for it that topic on social media or while surfing the internet, you have probably realized that it wasn’t a coincidence.
Google maps track your phone and the locations you frequent. Tracking this information allows Google to determine traffic issues, faster routes, and accident locations.
Companies have been known to track emails within the company and track sites visited on business computers. Misuse of these platforms has translated into employees getting fired.

Aerial Surveillance
Aerial surveillance is gathering visual information from airborne resources. Airborne resources can come from drones, UAVs, planes, and helicopters.
Private Investigators have been known to use devices like the DJI Mini to observe locations that are not easily reached to see a layout of an area, structures, and vehicles. Drones have become incredibly sophisticated with their technology while still being user-friendly. Invasion of privacy is still a concern with the use of these devices by investigators.
Law enforcement is using these drones in different capacities to cover amounts of territory quickly with less expense and resources (planes, helicopters, folks on the ground).
Drones and UAVs are used by the military in various capacities as well. The military uses aerial vehicles for surveillance, reconnaissance, threat assessments, and battle damage assessments.

Telephone Surveillance
Telephone surveillance can happen in many ways. It can come in the form of wiretapping, stingray boxes, and cellular triangulation.
Wiretapping
Wiretapping is recording communication between people, most often without their consent. It is illegal for citizens to wiretap however it is not unlawful for law enforcement to conduct a wiretap if they have a wiretap order. Law enforcement must prove that listening to your conversation will help with a crime that includes terrorism, drug trafficking, or money laundering.
Law enforcement can’t listen indefinitely. There are time limits given to wiretapping for law enforcement.
There are variations of wiretapping that don’t require a wiretap order. “Tap and Trace” as well as “Pen Registers” don’t require an order.
These less intrusive methods don’t record conversations however they track phone numbers associated with the phone line. These two methods track incoming calls and outgoing calls.
Stingray Boxes
Stingray Boxes are cell tower simulators. The cell phone tower simulators trick cellphones into transmitting the phone’s location and identifying information according to the ACLU. When used to track a suspect’s cell phone, it also obtains information about anyone else in the area who is not the subject of an investigation.
Cellular Triangulation
Cellular triangulation is used by law enforcement to locate however sometimes this information is inaccurate. 911 call centers in many cases have the technology to identify exactly where a is coming from which helps officers and 911 call receivers serve the community better.
Cell Phone Tracking
Cell phone and smart device locations come from 5 locations which are:
Historical CSLI (Cell-site location information)
With Historical CSLI law enforcement can use this data to determine areas someone has been because it provides a time stamp every time a phone connects to a cell tower.
Real-Time CSLI
With Real-Time CSLI a service provider (T-mobile, Verizon, AT&T) can monitor a phone location or ping a cellphone to reveal its location. Police can use this information to find a subject.
GPS Movement
A phone’s GPS system tracks its location using satellites. This information is stored and can be viewed in real-time by law enforcement.
Tower Dumps: Reverse Location Search
Instead of law enforcement requesting specific phone numbers and historical tower ping data, law enforcement can request all information from a specific tower at a specific time.
Geofence: Reference Location Search
A geofence is a search of a location history database to determine what devices were in a certain area at a certain time.
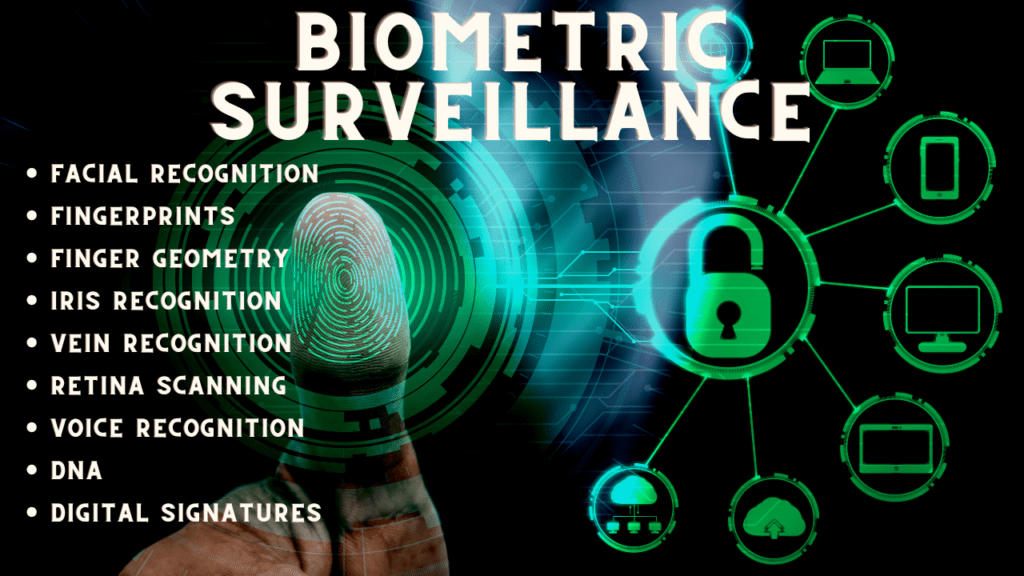
Biometric Surveillance (or Biometric Security)
Biometrics is the analysis and measurement of people’s unique characteristics both physical and behavioral.
Types of Biometrics Include:
- Facial Recognition
- Fingerprints
- Finger Geometry
- Iris Recognition
- Vein Recognition
- Retina Scanning
- Voice Recognition
- DNA
- Digital Signatures
Facial Recognition
Facial recognition is used in our everyday lives. We open our cell phones and tablets with this technology. Many computers use fingerprints to unlock computers.
If you have photos, some phones, and other photo-saving applications will be able to find photos with specific people in them.
Police use this technology to identify individuals who have been captured in video and photos committing crimes. It has also been used by the postal service but for reasons that are unrelated to crimes as previously spoken about.
Retina Scanning
This technology has been used with Clear. Clear uses retina scanning identification to get you through the airport more quickly. When signing up for clear the system gets a retina scan and a fingerprint scan.
Retinal scanning as well as Iris scanning has been declared as one of the most reliable biometric modalities, even better than fingerprinting.
This sort of scanning is typically used in high government agencies and is said to be used with ATMs and in the prevention of welfare fraud.
DNA Matching
DNA matching or fingerprinting is a chemical test that shows the genetic makeup of someone. Most people are familiar with this as it relates to solving crimes.
It is also used in other ways like helping to find blood relatives and finding cures for diseases.
Family members have been accidentally found by using services like:
Please note that the New York Times indicated that Family Tree DNA voluntarily provides customer data to law enforcement.
Fingerprints
Fingerprints have been used for over 100 years in tracking criminals and identifying noncriminals as well.
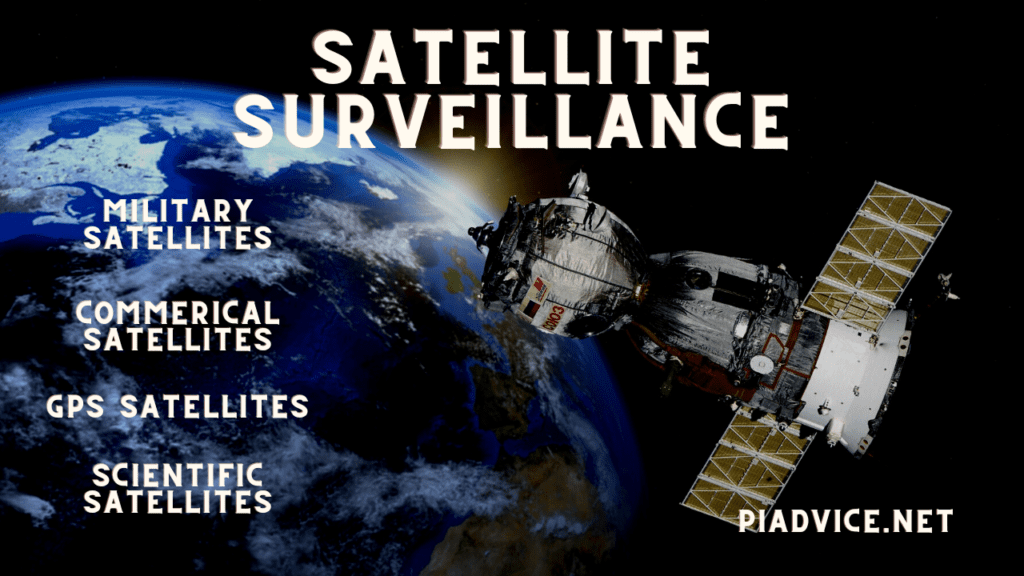
Satellite Surveillance (photos)
Satellite photos are far beyond just helping the military or government. Satellites provide us with images like Google Maps. This technology allows anyone to see any part of the world.
The different types of satellites that have been in the sky historically have been:
Military Satellites
These satellites are used for defense and intelligence.
Commercial Satellites
These satellites are for entertainment, mapping, and communication purposes.
GPS Satellites
These satellites support navigation systems.
Scientific Satellites
These satellites are used for climate studies, space research, and evaluating the earth and weather to name a few things.
Surveillance In the World
As technology continues to evolve for the better, people will find ways to perverse the technology for criminal purposes.
There are so many different types of surveillance technology and techniques, that we also have to make sure that this technology is not abused by the government and law enforcement agencies.
Private investigators also need to be vigilant in policing their own industry and not blur the lines between information finding, breaking the law, or invading an individual’s privacy. If you would like to read about what a private investigator can not do, you can see that here.
Recent Posts
Hawaii is probably one of the most interesting states to work as a private investigator if you are not used to the culture or a native of the state. And if you are not a local, that is something...
How to become a private investigator in Georgia